Protecting The World's Most Sensitive Data and Infrastructure
FV Deception
A protection system based on Deception technology, which allows you to create digital duplicates of devices to lure cyber attacks on yourself, protecting the
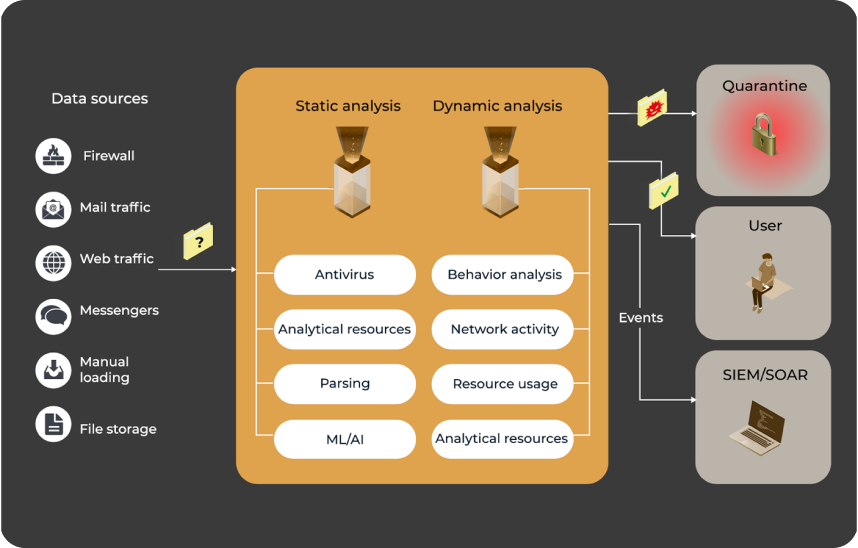
FV Secure Sandbox
A system based on sandbox technology to protect workstations, servers, databases and file storages from malicious software by checking files and security links.
FV SRM
World’s first Mass Sensor-based Spectrum Risk Management (SRM) Platform. Designed for large scale in-/out- door deployments, unique AI & ML ...
For oil & gas
Problem statement The industrial and manufacturing industry is the one of the most targeted sectors for cybercrime, together with finance and government sectors. According

Cyber security for banks
PROBLEM STATEMENT Sources of cyber attacks Internet Corporate mail USB devices Mobile devices According to IBM and the Ponemon Institute, the average cost of
Problem statement
of the most targeted sectors for cybercrime, together
with finance and government sectors.
to machinery.
We provide solutions that will help
to avoid data leakage and
protect from cyberattacks
Our Solutions
Solution for corporate sector

Purpose:
- Protection of electronic correspondence, legal and financial documentation
- Increase the level of protection against hackers penetrating industrial network
- Modeling risks for critical systems, enhanced training for IT security specialists
- Mitigate the risks of production shutdown, industrial equipment failure, accidents
Solution for industrial sector
Purpose:
- Traps can imitate any IT infrastructure objects:WEB server, FTP server, E-mail server, Workplace, Firewall, OS, Router, Switch, IoT / IIoT equipment, etc
- The elements (sensors) are deployed on each company network (VLAN) and connected to the management module
- Each element (sensor) deploys a set of traps corresponding to real devices, computers and services on the network
- An additional important feature of the system is the built-in vulnerability scanner. Each element (sensor) in the system can scan its network for vulnerabilities.
GET ADVICE FROM OUR EXPERT
We will find a reasonable solution to your task. Expert reply in one day.